Security Audits – What They Are and Why They Matter
Writing code is a long error prone process for even the most experienced programmer. Writing secure code for encryption requires advanced knowledge in multiple completely independent fields of computing including secure programming methods, hardware, operating systems, advanced mathematics, and a strong grasp of common attacks against the kind of code you are creating. In a world where a tiny gap of knowledge in any of these topics can create a void that gets exploited by criminals and governments alike it takes extraordinary vigilance to verify the integrity of code and ensure that experts agree that the code is invulnerable to all known attacks.
The OSTIF periodically gets code audited by elite professionals (both companies and individuals), who comb through the code line-by-line and look for possible exploits. It is important that open source security software goes through this process on a regular basis as the code is so complex that only a handful of people (less than 10000) in the world are truly qualified to audit it with the level of scrutiny that allows the entire world to trust their results.
Auditing is a complex and labor-intensive process. The most simple type is basic scanning by specialized software to look for errors in code that can lead to security vulnerabilities. There’s also more complex types which involve looking at the code line-by-line for common coding errors that software will routinely miss, but still create flaws, and the most advanced type of auditing involves threat modeling, which is the process of figuring out the sophistication of a likely attacker, and how they would try to attack the software, and then manually searching for flaws in the software based on how it actually behaves, as well as taking a look at the most important pieces of the source code. OSTIF hires individuals and firms to look at the source code of the supported applications using all of these available methods.
The process is detailed in the image below!
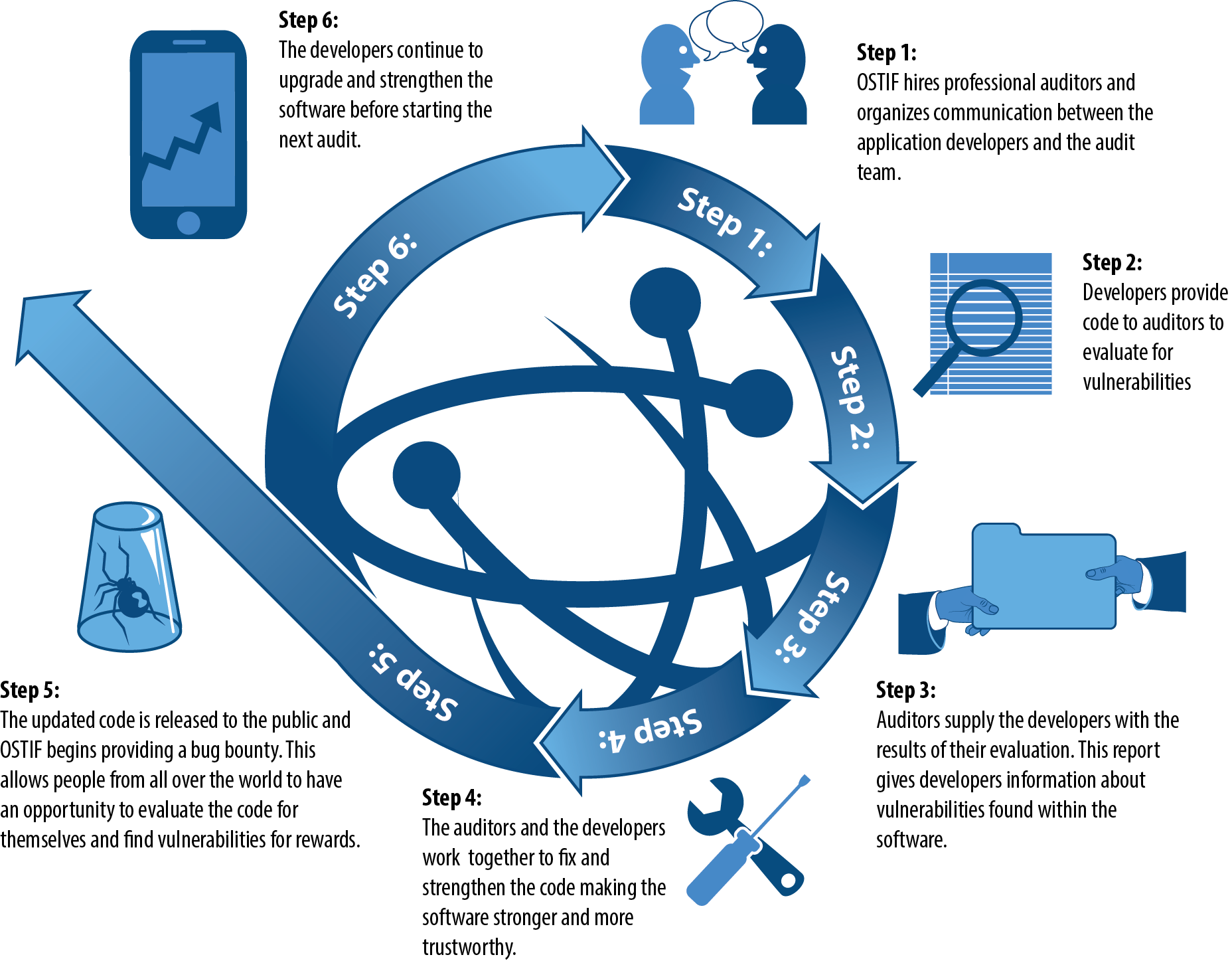
This, combined with our commitment to maintaining bug bounties, will allow continued external community support for the projects that is crucial to building trust and the strongest possible software engineering.